Blocking Group Policy
You’re on an engagement and just obtained your first set of credentials. Score! You attempt to join your Windows VM to the domain and you are greeted with a warm message: “Welcome to the __ domain”. You’re excited to have your initial foothold in the network but you quickly realize these credentials don’t provide much access. We need to go deeper!
You start looking for ways to elevate your access in the network. Should we gather a list of Active Directory users for a reverse bruteforce? Perhaps there’s a set of local admin credentials tucked away inside GPP? Or maybe you already have access to a host that has Domain Admin credentials in memory but you don’t know it yet- Bloodhound to the rescue!
Wait! Let’s pump the breaks a bit. The benefits listed above don’t come without a drawback. Do you realize that by joining your VM to the domain, you’ve effectively granted Domain Administrators access to it? In order to prevent Group Policy from adding any unwanted restrictions or unauthorized access to your Windows VM you should disable the Group Policy Service.
Warning: Standard local user accounts will not be able to log in after this change. Therefore this configuration should not be applied to machines that are meant for actual production use since it is best practice to log in as a standard user.
1. Open regedit
2. Navigate to the Services tab. HKLM\SYSTEM\CurrentControlSet\services
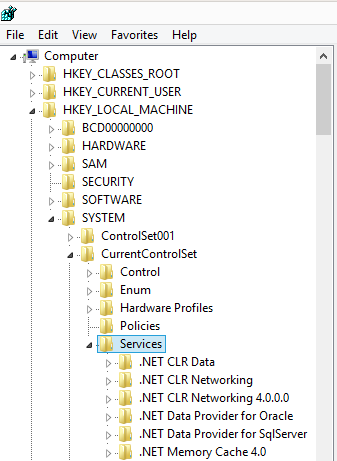
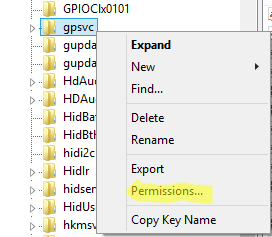
3. Now scroll through the list until you find the “gpsrv” key. Right click on it and select Permissions
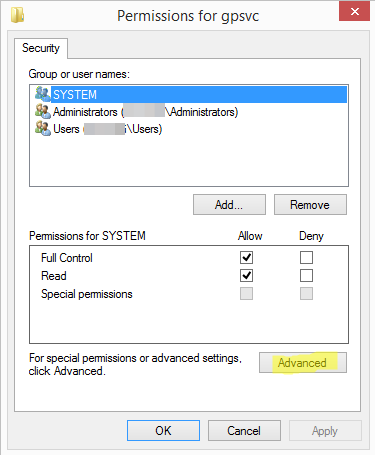
4. Select Advanced
5. Click Change
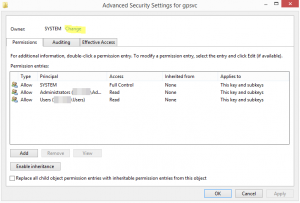
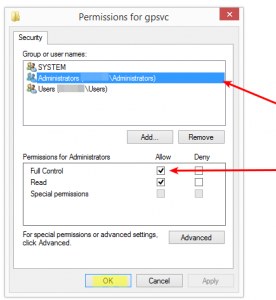
6. Click Administrators and then check Full Control and click OK
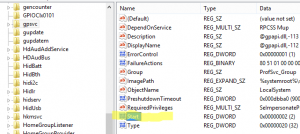
7. Double click the Start key under gpsvc
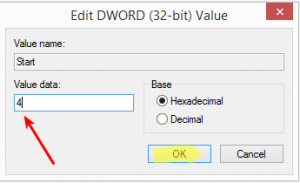
8. Change the value to 4.
The value 4 sets the Group Policy service to “Disabled”. Other values include: Automatic – 2 Manual – 3
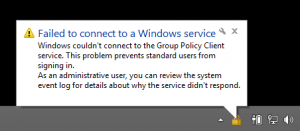
9. Ater a reboot you will see the following message. Now domain Group Policies will not be applied to this machine.