Introduction
On one of our recent engagements we were tasked with testing a network protocol for DoS conditions. Naturally this engagement led us to explore the various fuzzers that are currently available. After going through a few options, I came across a python fuzzing framework on Github called Sulley. The framework looked to be unmaintained, which led to the discovery of boofuzz. Boofuzz is a fork of the Sulley fuzzing framework and is actively maintained.
What is fuzzing?
Fuzzing is the act of sending random data into software in the hopes that you cause a crash. A crash could mean that user input is mishandled in some fashion, which could lead to exploitation. Not all crashes are exploitable, sometimes you may just cause a DoS condition.
Boofuzz is a python fuzzing framework. It’s capable of fuzzing a target and automatically restarting a process in case of a failure. While this is nice, it wasn’t relevant to the engagement as there would be no access to the binaries which we were targeting. As a result, I won’t be covering that in this tutorial. If you would like to see an example of automatically restarting a process you can visit this blog. While it’s written for the Sulley framework, it’s still applicable to Boofuzz.
Required files:
To get started, you will want to install python 2.7.9 run:
pip install boofuzz
You will also need to clone the example files from my github.
Scenario:
boofuzz_server.py only has one valid command “HELLO”. We want to fuzz this command to ensure it is stable enough for production. To start boofuzz_server.py, simply type:
python3 boofuzz_server.py
Teach boofuzz about the HELLO command:
In order to fuzz the HELLO command, we need to teach boofuzz how to interact with the boofuzz_server. Boofuzz refers to this as grammar. Grammar is any code that starts with “s_”. Look inside of the file “network_protocol_example.py” and you will find a grammar section right at the top. Here’s a breakdown of the grammar:
s_initialize(‘grammar’) # Name of the following instructions
s_static(“HELLO\r\n”) # Always send this. Don’t modify it.
s_static(“PROCESS”) # Send right after HELLO\r\n
s_delim(” “) # Delimiters will be swapped during the session
s_string(“AAAA”) # This is our base fuzzing string
s_static(“\r\n”) # Tells the server “Done”
Action:
To start the fuzzer, all you must do is run network_protocol_example.py. You must make sure boofuzz_server.py is running first, otherwise you will receive an error. These examples will work out of the box with no configuration or command line arguments required.
Immediately you will notice boofuzz tries a new test case every 2 seconds (you can modify this with the “sleep_time” option in network_protocol_example.py) and provides you with information on each test case:
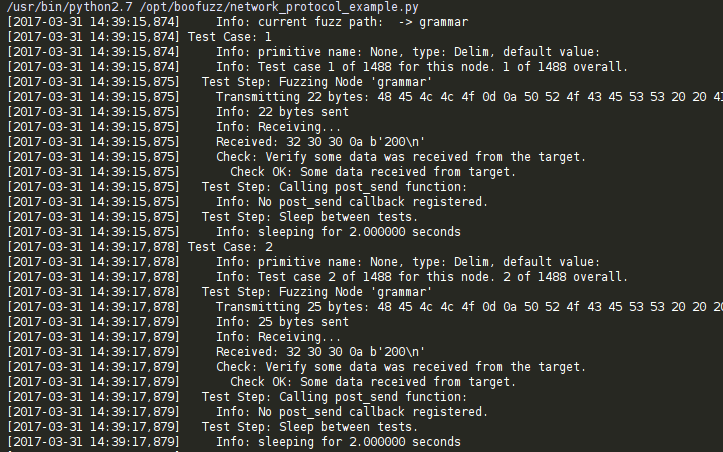
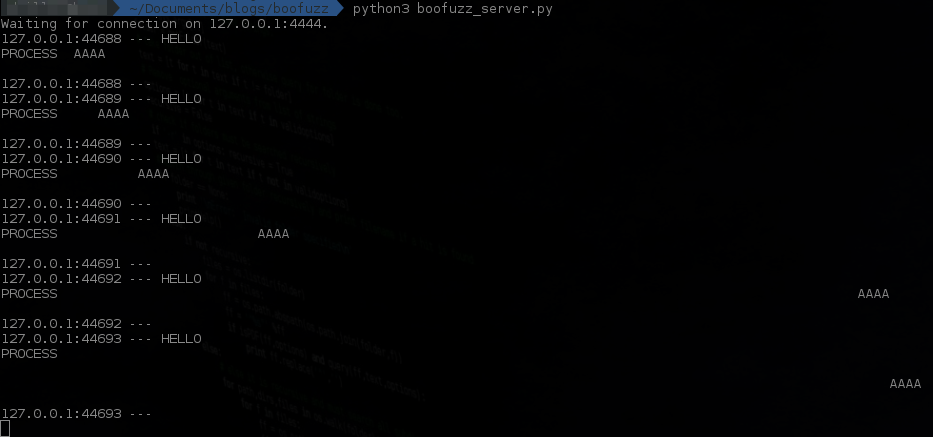
From boofuzz_server.py you will be able to observe the different attempts boofuzz makes at sending malformed data. Don’t worry, it tries more than just AAAA combinations:
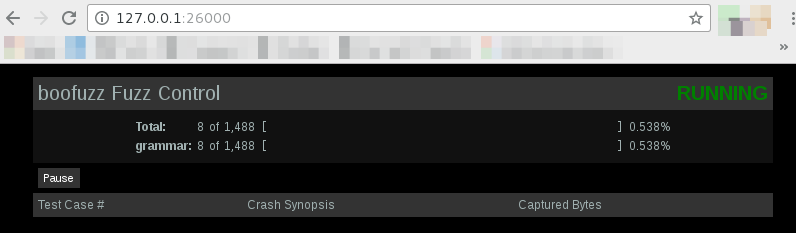
Lastly while boofuzz is running you are able to visit http://127.0.0.1:26000/ and view statistcs on your overall progress. You will have to refresh the page to get updates:
Overall I believe boofuzz is a pretty solid starting point for simple fuzzing. With that being said I believe it lacks documentation to help new comers get started. I’d also like to see live updates through the web page and perhaps more detailed information about test cases. Regardless, I’d definitely recommend giving this tool a try.